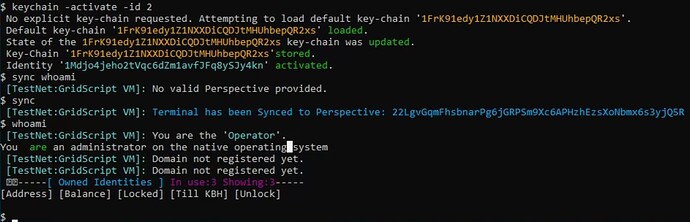
During the initial bootstrap sequence you should be able to see lines reassembling ones below:
[TestNet:Blockchain Manager]: Operator's Key-Chain ID: key0
[TestNet:Blockchain Manager]: Operator's State Domain ID: 159G9aduJHQ1iSRK3N4cBoJ8Nc35Vuiynq
[TestNet:Blockchain Manager]: Note: Your current ID within the network is: 159G9aduJHQ1iSRK3N4cBoJ8Nc35Vuiynq use 'getNextID' to generate and set new ID from your key-chain at any moment.
Notice above that reportedly your main key-chain is key0 (the default).
A single key-chain may own very many sub-identities, each representing a unique State-Domain (wallet’s address for basic usage scenarios).
Now, once you run keychain -show you would see something reassembling what’s shown below:
$ keychain -show
Use '-help' to see available options.
No explicit key-chain requested. Attempting to load default key-chain 'key0'.
Default key-chain 'key0' loaded.
v--[Key-Chain Data]--v
[Name]: key0
[Active Identity At Index]: 0
[Key-Chain Depth]: 2
[Active Domain]: 159G9aduJHQ1iSRK3N4cBoJ8Nc35Vuiynq
v--[All Domains]--v
0) 159G9aduJHQ1iSRK3N4cBoJ8Nc35Vuiynq
1) 1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c
as you can see currently there’s an identity active at index 0. To be precise we have actived the sub-identity 159G9aduJHQ1iSRK3N4cBoJ8Nc35Vuiynq from the key-chain, which is at index 0 of your key0 key-chain.
To switch identity, say to identity at index 1 we need to use:
keychain -id 1 -activate
see below:
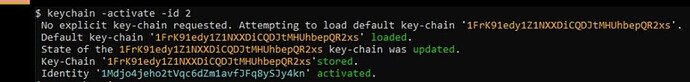
$ keychain -id 1 -activate
No explicit key-chain requested. Attempting to load default key-chain 'key0'.
Default key-chain 'key0' loaded.
State of the key0 key-chain was updated.
Key-Chain 'key0' stored.
Identity '1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c' activated.
now once we execute keychain -show it would report what follows:
$ keychain -show
Use '-help' to see available options.
No explicit key-chain requested. Attempting to load default key-chain 'key0'.
Default key-chain 'key0' loaded.
v--[Key-Chain Data]--v
[Name]: key0
[Active Identity At Index]: 1
[Key-Chain Depth]: 2
[Active Domain]: 1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c
v--[All Domains]--v
0) 159G9aduJHQ1iSRK3N4cBoJ8Nc35Vuiynq
1) 1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c
It thus successfully activated State-Domain 1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c available at index 1 of your key0 key-chain.
You may have multiple key-chains.
Now, if we reboot Core, during the initial bootstrap sequence we would see what follows:
[TestNet:Blockchain Manager]: Operator's Key-Chain ID: key0
[TestNet:Blockchain Manager]: Operator's State Domain ID: 1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c
[TestNet:Blockchain Manager]: Note: Your current ID within the network is: 1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c use 'getNextID' to generate and set new ID from your key-chain at any moment.
Worked 100%. Your new identity is active and the setting would prevail during restarts.
Operator, now if you run keychain - help you would see a plethora of explanation and additional documentation including examples.
Part of this built-in MAN-page follows:
[Arguments]:
- qr: Use a QR Intent for export which may be scanned by the mobile application.
- gen: Generate a new key-chain.
- name: Includes key-chain's name in exported data.
- store: Store the key-chain in cold storage.
- activate: Activate a key-chain as the main identity. Defaults to index 0 if not specified.
- export: Export a key-chain. Use with '-master' to export the master key.
- master: Used with 'export' to export the master key.
- name [chainID]: Name the key-chain. Defaults to 'keyX' where X is a number.
- genid: Generates the next unused sub-identity.
- id [index]: Set an active sub-identity index.
- show: Display key-chain information. Use '-priv' to include private key.
- priv: Used with 'show' to display the private key.
The getnextid GridScript command is now deprecated. The new keychain utility is your power-house for all identity and key-management needs.
Let’s use the -genid switch to generate an additional sub-identity, shall we?
$ keychain -genid
Use '-help' to see available options.
No explicit key-chain requested. Attempting to load default key-chain 'key0'.
Default key-chain 'key0' loaded.
Most recent identity at index 1. Getting new identity at index 2
Remember to use '-activate' to actually activate this identity.
State of the key0 key-chain was updated.
Key-Chain 'key0' stored.
Identity '1GSDYfFmaWhUzg3ZVr5Gn2Qde2KCHkKWuH' activated.
Operator, notice! While it generated new identity the output deliberately explains that
- it was not activated
- it was not saved
thus, in fact your key-chain or Core’s settings were not affected in any way!
For these settings to be effective you need to use -activate switch so the final command would be
keychain -genid -activate or at least keychain -genid -store to be able to see the activity with consecutive calls to keychain -show.
Activating an identity within of a given key-chain implicitly causes the encapsulating key-chain to be assumed as the main Operator’s key-chain as well.
Next time you run key-chain -show you would see:
$ keychain -show
Use '-help' to see available options.
No explicit key-chain requested. Attempting to load default key-chain 'key0'.
Default key-chain 'key0' loaded.
v--[Key-Chain Data]--v
[Name]: key0
[Active Identity At Index]: 2
[Key-Chain Depth]: 3
[Active Domain]: 1GSDYfFmaWhUzg3ZVr5Gn2Qde2KCHkKWuH
v--[All Domains]--v
0) 159G9aduJHQ1iSRK3N4cBoJ8Nc35Vuiynq
1) 1BhQ3h9VqbXKzjWNkPhRYqTbhJZ2xiUQ7c
2) 1GSDYfFmaWhUzg3ZVr5Gn2Qde2KCHkKWuH