June 20 - July 17th, 2025
Executive Summary
TLDR:  A brief visual (animated) representation of everything described herein is available
A brief visual (animated) representation of everything described herein is available  here
here
Also: join our Discord Live-Development channel for hourly updates almost 24/7 here.
GRIDNET OS, positioned as the world’s first decentralized operating system, has faced sustained and sophisticated attacks across multiple vectors throughout this reporting period. The development team, working transparently on YouTube LIVE, has documented their battle against both infrastructure-level DDOS attacks and financial market manipulation on the Xt.com exchange. This report details the daily progression of attacks and countermeasures, highlighting the challenges faced by disruptive blockchain projects attempting to challenge the established crypto ecosystem.
Overview of Attack Vectors
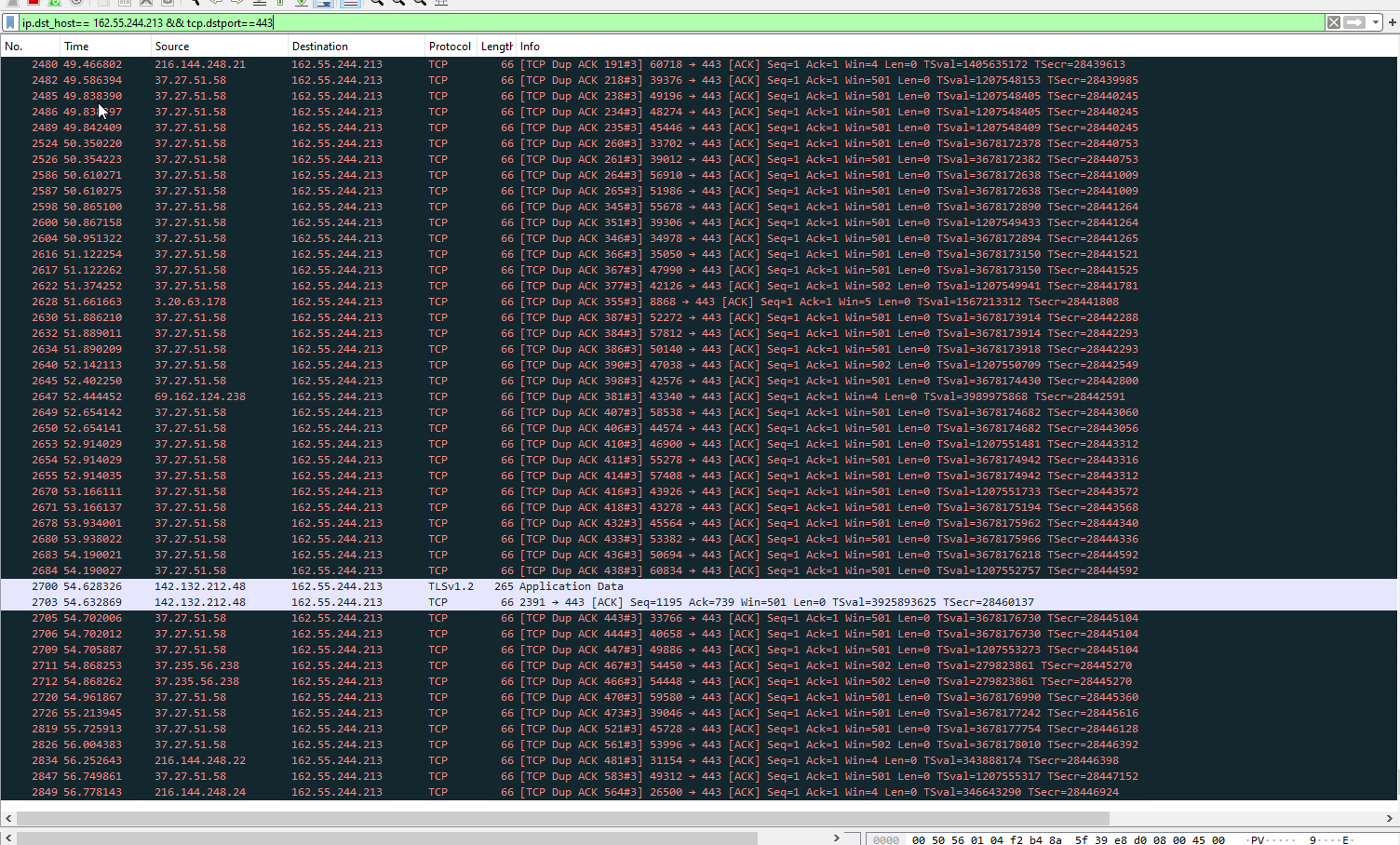
1. Infrastructure DDOS Attacks (June 20-29)
The attacks began as sophisticated Slowloris attacks targeting the HTTP protocol implementation in GRIDNET Core’s web server infrastructure. These evolved into:
- Slowloris attacks: Exploiting connection timeouts in the Mongoose web server library
- SYN flood attacks: Overwhelming the Windows connection backlog
- HTTP/1.1 persistent connection exploits: Using Keep-Alive features for sustained attacks
- WebSocket upgrade attacks: Targeting the HTTP-to-WebSocket upgrade sequence
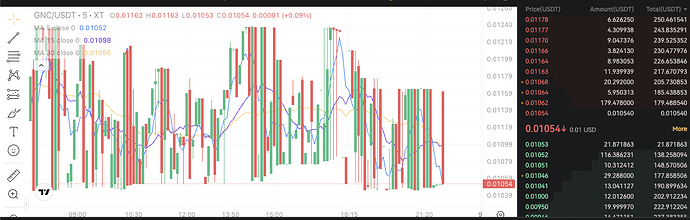
2. Market Manipulation on Xt.com (June 29 - July 9)
Following successful mitigation of infrastructure attacks, hostile actors pivoted to financial warfare:
- High-frequency pump & dump schemes: Artificial price inflation followed by coordinated dumps
- CEX Sandwich attacks: Exploiting market maker positions to drain USDT
- Bot-driven order book manipulation: 24/7 automated trading patterns
- Estimated losses: ~50,000 USDT/month under naive market making strategies
Daily Development Chronicle
June 20-21: Initial Slowloris Attack Response
The Emergency Response Team identified Slowloris attacks from Iranian nodes targeting the Mongoose web server library. Initial mitigation focused on:
- Analyzing LARS (presumably their monitoring system) crash reports
- Investigating Universal CRT library compatibility issues on Windows systems
- Implementing initial timeout and connection monitoring mechanisms
June 22: Escalation and Advanced Mitigation
- Attacks intensified, requiring service downtime
- Team implemented sophisticated HTTP request tracking
- Added data-rate sensing for both HTTP and WebSocket connections
- Introduced connection state monitoring with military-grade precision tracking
June 23: First Major Update Deployment
- GRIDNET Core 1.8.4 released through LARS
- Network propagation reached 80% within hours
- Revised anti-DDOS mechanics began reporting ongoing attacks
- Initial success in maintaining DUI (Decentralized User Interface) availability
June 24-26: Deep Protocol-Level Defense
The team transitioned to kernel-level defenses:
- Integration of Windows Filtering Platform (WFP) APIs
- Implementation of packet filtering before TCP handshake completion
- Custom WSAAccept callbacks to reject connections without consuming backlog slots
- Development of what they claim will be “the most advanced real-time DDOS mitigation system for Windows”
June 27-28: Stabilization and Counter-Intelligence
- Attacks continued but with diminishing effectiveness
- CPU utilization on AMD Threadripper systems remained low despite attacks
- Attackers banned at kernel mode before GRIDNET Core notification
- Team noted attackers would need “new techniques” to be effective
June 29: Pivot to Market Manipulation
- GRIDNET Core 1.8.5 deployed
- Infrastructure attacks largely neutralized
- Hostile actors shifted to Xt.com trading manipulation
- Team began investigating “gangsta bot” activity on the exchange
July 1-4: Understanding Market Attack Patterns
Detailed analysis revealed the attack methodology:
- Bot buys at price P1
- Price increases to P2 > P1
- Bot waits for market maker to offer USDT at new price
- Bot immediately sells, draining USDT
- Price returns to P1 or below
- Cycle repeats 24/7
Key findings:
- Xt.com allegedly ignored multiple reports
- Exchange suggested lowering spreads even further (which would increase losses)
- “ST” (Special Treatment) warning flag applied to GNC
July 5-7: Advanced Market Making Countermeasures
The team developed “Wizardly Liquidius Maximus,” incorporating:
Pump & Dump Detection:
- Multi-factor confidence scoring system
- Baseline price calculations using sophisticated clustering algorithms
- Real-time attack classification (Slow Pump, Fast Pump, etc.)
- Automated mitigation through strategic counter-dumps
Technical Innovations:
- Garman-Klass-Yang-Zhang volatility estimates
- Microstructure noise analysis for HFT detection
- “Flashing Order Book” implementation (orders appear/disappear at high frequency)
- Multi-threaded asynchronous order management
- Probabilistic order visibility (<50% visibility time to thwart bots)
Defensive Strategies:
- Creating “air pockets” on buy-side during detected pumps
- Immediate sell execution to prevent USDT drainage
- Synchronized spread partner management
- Quote asset volume assurance
July 5-6: Enhanced Market Defense Systems
- Implemented third-party depth hit-absorption ratio analysis
- Focused on risk assessment specific to market making accounts rather than entire market
- Added anti-flashing buy-side order detection to counter attackers who place orders briefly to fool algorithms
- Research Department provided continuous algorithmic improvements
- Market volatility assessment showed 80% despite bot attempts to mask it
July 7: Public Statement and Transparency
- Team published an official “Public Statement: Addressing Market Manipulation and Our Path Forward” on GRIDNET Talk
- Documented systematic market manipulation evidence
- Acknowledged the irony: “it is sad that a crypto project such as ours needs to resort to such methodologies, just to trick hostile bots active on a presumably reputable crypto exchange platform”
- Continued refinement of the “Epic Wizardly Liquidius Maximus” market making service
July 8: Infrastructure Update and Strategic Planning
- Tier 0 nodes confirmed stable for 14 days despite attacks
- Nodes taken down for 15-minute update
- Team announced 72-hour intensive focus on Pump&Dump and Sandwich attack prevention
- Maintained development schedule for:
- Wallet UI dApp (release by end of month)
- Mobile-app-less interaction with the system
July 9: Public Documentation and Multi-Exchange Planning
- Published comprehensive public statement detailing market manipulation tactics
- Team began incorporating multi-exchange API support infrastructure
- Noted that “Shitcoins and Memcoins seemingly not targeted but Bitcointalk fellas like us very very very MUCH”
- Revealed 2017 history: Bitcointalk community labeled them as ‘scammers’ despite continuous development
July 10-12: Advanced Flashing Order Book Implementation
The team achieved breakthrough improvements in their market defense:
Asynchronous Order Management:
- Massive improvement: transitioned to fully asynchronous (multi-threaded) task system
- Each order now operates on virtually separate thread
- Simultaneous toggling of multiple transactions
- API rate throttling module governance
Probability-Based Defense:
- Orders visible <50% of the time with randomized timing
- Hostile bot forced into “roulette” scenario
- Expected bot loss rate: ~70% of attempts
- Physics-based defense: “the flow of time” as protection mechanism
July 13-15: Fuzzy Order Book Technology
Development of revolutionary “Fuzzy World-View” system:
Core Innovation:
- Orders exist in probabilistic states
- Market making software maintains dual reality:
- External exchange API data
- Internal fuzzy probabilistic dataset
- Blended data provides superior market assessment
Technical Implementation:
- Synchronized spread partner identification
- Autonomous quote asset volume assurance
- Edge case handling for orders taken in 200-300ms windows
- Military-grade state machine transitions
July 16-17: Final Refinements and Observations
Suspicious Activity Detected:
- Team noted orders being taken when flashed for only 200-300ms
- “Would be suspicious to say the least - pending further verification”
- Suggests possible (close-to) exchange-level visibility into their system
Continued Development:
- Integration of flashing orders module with market view module
- Ensured external exchange data doesn’t distort fuzzy world-view
- Maintained transparency: “everything on YouTube LIVE - everything for YOU”
Updated Attack Pattern Analysis
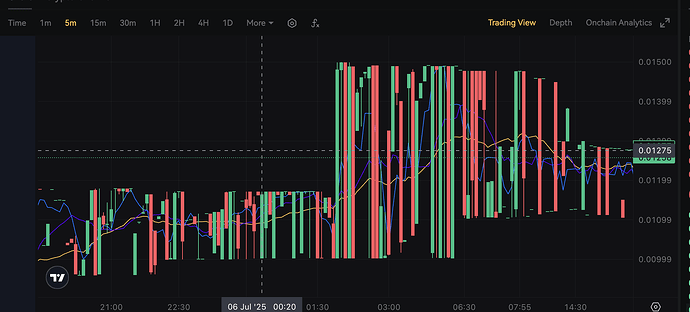
Evolution of Market Attacks (July 5-17)
- Adaptive Bot Behavior: Hostile bots attempted to decrease perceived market volatility to mask their activities
- Flash Order Targeting: Evidence suggests bots may have sub-second order detection capabilities
- Coordinated Suppression: Daily volume on Xt.com dropped to $150, effectively killing natural trading
Team’s Counter-Evolution
- From Reactive to Predictive: Shifted from responding to attacks to probabilistic defense
- Multi-Threading Success: Achieved true high-frequency market making capabilities
- Mathematical Superiority: “We’ve got better mathematicians, and we’ll be acting accordingly”
Key Revelations from Extended Period
Exchange Complicity Indicators
- Orders taken in 200-300ms windows suggest information leakage
- Xt.com’s continued inaction despite documented manipulation ( they’ve claimed to disabled some accounts with suspicious activities, but you may see the oscillating USDT sucking pattern since the day we got listed).
- Market making rules “literally create a perfect environment for bot operators”
Global Ambitions Despite Attacks
- Planning to offer Wizardly Market Making as a service to other projects
- Specifically targeting projects attacked by “malicious organizations such as PWTG and Bitcointalk”
- Vision: Enable defense for all disruptive projects facing establishment resistance
Technical Innovations (July 5-17)
1. Flashing Order Book System
- Revolutionary approach using quantum-like probabilistic states
- Orders exist and don’t exist simultaneously
- Forces attackers into unfavorable probability games
2. Multi-Reality Market Assessment
- Maintains multiple versions of market truth
- Blends exchange API data with internal probabilistic model
- Superior decision-making through uncertainty principle
3. Asynchronous Defense Architecture
- True parallel processing for order management
- Microsecond-precision timing control
- Rate-limited but not rate-constrained
Final Assessment
The extended period from July 5-17 shows an escalation in both attack sophistication and defense innovation. The team’s progression from basic timeout mechanisms to quantum-inspired probabilistic market making represents one of the most advanced responses to market manipulation in crypto history.
Most tellingly, at some moments in time, their observation of 200-300ms order captures suggests the battle has reached a new level— hopefully the exchange itself is not providing unfair advantages to attackers (too early to assume, no proofs). Overall, the undeniable oscillating pattern since the day of listing, validates their earlier suspicions and reinforces the narrative of institutional resistance to disruptive projects.
The team’s commitment to transparency (everything on YouTube LIVE) while building military-grade financial defense systems sets a new standard for how innovative projects can resist coordinated suppression attempts. Their plan to offer these defenses to other targeted projects could mark a turning point in the ongoing war between crypto innovation and establishment interests.
Analysis: The Crypto Establishment’s Resistance
The development team’s documentation reveals a pattern consistent with coordinated resistance against disruptive projects. Key observations:
- Targeted Nature: As noted by the team, “meme coins and shitcoins” are not subjected to these attacks, only projects with potential to “dethrone Fat Cats”
- Multi-Vector Approach: When infrastructure attacks failed, adversaries seamlessly transitioned to market manipulation
- Institutional Complicity: Xt.com’s alleged refusal to address obvious bot manipulation, despite documented evidence, and hilarious spread lowering suggestions suggests only fuels conspiracy theories.
- Resource Intensity: The sophistication and persistence of attacks indicate well-funded opposition
- Historical Context: Team mentions being labeled “scammers” on Bitcointalk since 2017, despite continuous development
Technical Achievements
Despite constant attacks, the team achieved remarkable technical milestones:
- Kernel-Mode DDOS Protection: Custom Windows Filtering Platform integration surpassing commercial solutions
- Advanced Market Making: Algorithms rivaling those used by firms like Wintermute Trading and Jump Trading
- Real-Time Transparency: All development conducted live on YouTube, providing unprecedented accountability
- Rapid Response: Updates deployed within hours of attack detection
Conclusion
The GRIDNET OS team’s experience exemplifies the challenges faced by genuinely disruptive blockchain projects. Unlike meme coins that pose no threat to established interests, projects attempting fundamental innovation face:
- Coordinated technical attacks requiring military-grade defenses
- Financial warfare through market manipulation
- Institutional resistance from exchanges
- Reputational attacks from established crypto communities
The team’s response—building increasingly sophisticated countermeasures while maintaining complete transparency—demonstrates both the severity of the challenge and their commitment to persevering. Their claim that “we become stronger each and every day” appears validated by their technical achievements under fire.
The message is clear: disrupting the crypto establishment requires not just innovative technology, but the resources and expertise to defend against inevitable retaliation from those with vested interests in maintaining the status quo.