Download URL: https://gridnet.org/GRIDNETCore.zip
Release Notes:
Hey folks! What’s up! This was supposed to be Release Notes of version 1.0.6 so why 1.0.7 all of the sudden, huh? Testing, testing, hot-patching… things move around rather fast around here… anyway! Let us go, let us flow (…) the glory of Decentralization it awaits! So, let us take a look (…)
Lots and lots of changes and improvements (yet again…)
- the JavaScript-based ⋮⋮⋮ Decentralized Boot-Loader received a huge revamp.
We’ve actually added a brand new (now acting as initial) stage which verifiers all the nodes which are being discovered through our variance of Kademlia decentralized ⋮⋮⋮ Peers’ Discovery Protocol.
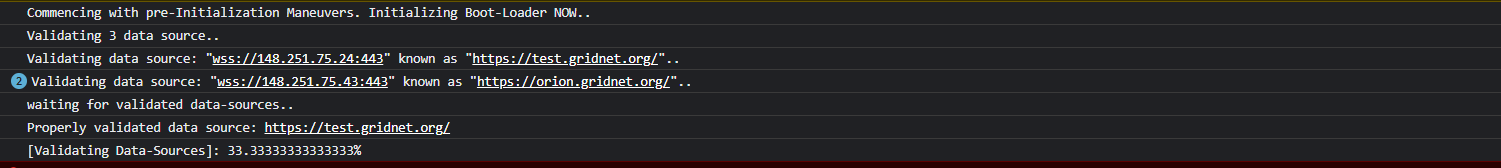
The number of validated data-sources is updated on screen as these are verified:
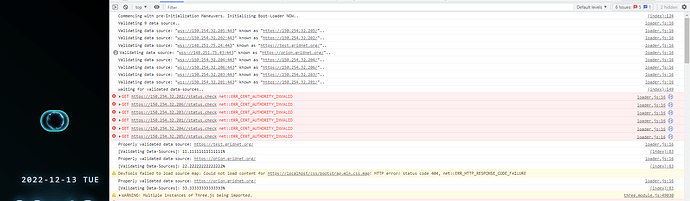
Feel free to switch to the more detailed Developer’s Pane of Chromium (CTRL+SHIFT+I) to see these validations taking place in much more detail:
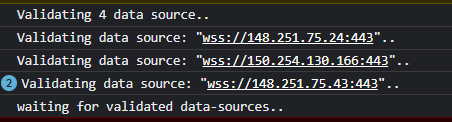
Why was that needed? Well, our network is now fully decentralized.
With that said, we have no control over ⋮⋮⋮ Nodes operated by others. As ⋮⋮⋮ Nodes are discovered, these are injected to ⋮⋮⋮ Node’s JavaScript-based Bootloader, which up until now were unable to verify whether the actual assets were reachable and blindly attempted to fetch the assets.
Now the question is - why the assets would not be reachable in the first place?
Simple. Nodes might be behind a variety of NATs / firewalls which, when not properly configured, might thwart access to resources. Also, resources might not be available from a particular node due to invalid TLS certificates and a variety of custom settings imposed by a particular web-browser and/or client’s Internet Service Provider.
So, the bottom line is - now ⋮⋮⋮ Bootloader, verifies and validates access to assets from each discovered peer before assuming it as an appropriate data-source. That immensely improved reliability of the ⋮⋮⋮ Decentralized User Interface Loading mechanics.
There’s more…
- improved protection against network eclipsing attacks
Now, each node will attempt to keep a connection with at least one of the ‘official’ nodes to improve resilience against malicious nodes and network eclipsing attacks. These connections and or data from these nodes are not prioritized in any way.
- yet again - improved performance of synchronization (lots of changes here)
As we’ve already mentioned on Twitter, we’ve been improving synchronization performance for when the history of events of the ⋮⋮⋮ Decentralized State-Machine grows.
What’s so special about the cases at large block heights?
The exchanged ‘chain-proofs’ (proving the history of events, without nodes needing to download the actual data-blocks) between ⋮⋮⋮ Nodes used to get bigger and bigger. Not only did it impose excessive network-overheads, but the processing power needed to analyze these by recipients grew linearly with a given block height of the current leading block.
That processing used to take place within a thread responsible for a given conversation, which could lead to connections being dropped, as not even keep-alive signals were to be exchanged as the recipient verified a provided chain-proof.
So we went ahead and optimized this a lot.
The exchanged chain-proofs are now very minimal. And both the processing power and network overheads are orders of magnitude smaller. Not only that. We’ve also introduced protection against evil nodes which would attempt to enforce processing of large chain-proofs onto others.
-
added an additional REST service to GRIDNET Core which would provide information regarding current status of each particular node to the JavaScript-based bootloader.
-
improved connections’ management. We test everything 24/7 when anything goes wrong we jump straight into the action and fix things. The overall stability of connections between nodes has been yet again improved.
-
improved reporting and logging
-
security improvements
-
yet again minimized mutex-congestion, leading to better overall performance
-
other minor changes
-
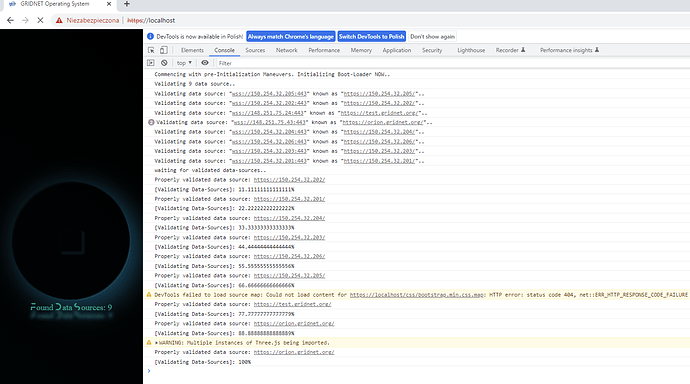
improved support of internal DNS mechanics by the ⋮⋮⋮ Bootloader:
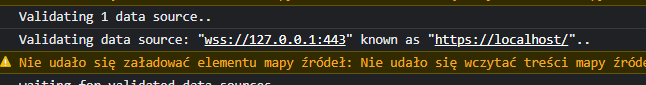
or it’s probably even better visible below:
Chromium requires content served by TLS certificates to be accessed from computers pointed to by the Centralized global DNS system (at least in its default configuration), thus we make our internal DNS system translate IPs to known domains. We’ll be making utilities and commands available which would allow for you to register decentralized domains of your own, for now - should you wish to have a node registered within our own domain at *.GRIDNET.ORG simply do let us know and we would issue a certificate and a sub-domain so that you could use it ex. ‘orion.gridnet.org’ or whatever you come up with.