Securing the Network: GRIDNET Core 1.5.5’s Revolutionary Integrity System
In the ever-evolving landscape of cryptocurrency mining, security isn’t just a feature – it’s fundamental to the ecosystem’s survival. With the release of GRIDNET Core 1.5.5, we’re introducing a groundbreaking approach to system integrity that sets new standards for mining software security.
Why Integrity Matters
Imagine you’re running a race where some participants have secretly modified their running shoes with hidden springs. No matter how fast you run, you’re at a disadvantage before the race even begins. This scenario parallels the challenges faced in cryptocurrency mining when kernel files can be manipulated for unfair advantages.
But the stakes are even higher. A compromised mining core doesn’t just affect individual operators – it threatens the entire network’s integrity. Whether through malicious modification or accidental corruption, any tampering with the Core or its kernel files can create an uneven playing field that undermines the fundamental principles of fair mining, or in the GRIDNET OS specific parlance - Operating. Indeed, in GRIDNET OS - Operators are involved in so much more then what they’ve known from prior Layer-0 generation systems such as Bitcoin, Ethereum or Solana.
The Innovation Behind the Security
GRIDNET Core 1.5.5 introduces a fascinating solution to this challenge through an innovative application of cryptography and binary manipulation. At its heart lies a clever mechanism that turns the executable itself into its own integrity validator.
The most intriguing aspect of this implementation is how we solved the “chicken and egg” problem of self-validation. How do you store a hash inside a binary file while ensuring that the stored hash itself doesn’t affect the final hash calculation? Our solution employs a technique we call “anchored padding.”
Think of it like a ship’s manifest that must list its own weight without affecting the ship’s total weight. We accomplished this by creating a fixed-size region in the binary’s data section, marked by distinct prefix and suffix patterns, for ease of visualization you make imagine these as follows : “----|” and “|----”. Between these markers, we store our validation data using a combination of Base58Check encoding and ChaCha20 encryption, padded with asterisks to maintain a constant size.
The real magic happens in the PE (Portable Executable) file handling. Instead of hashing the entire executable, we focus exclusively on the code section (known as the .text section in PE format). This section contains the actual program instructions, remaining constant across different installations while excluding variable elements like resources and data sections.
Technical Deep Dive
The integrity validation process is an elegant dance of cryptographic operations. When the Core launches, it performs a precise surgical operation on its own binary file:
- It maps its own executable file into memory and navigates the PE header structure to locate the code section.
- A SHA-256 hash is computed over this code section, carefully avoiding the region containing our stored hash.
- The resulting hash is encoded using Base58Check – a format familiar to cryptocurrency enthusiasts – which provides both human readability and error detection.
- This encoded hash is compared against a decrypted version of our stored hash, with the ChaCha20 encryption providing an additional layer of tamper resistance.
The beauty of this system lies in its deterministic nature. Every bit of the code section contributes to the final hash, making it computationally infeasible to modify the code while maintaining the same hash value. Yet, through careful segregation of code and data sections, we ensure that the stored hash itself doesn’t create a circular dependency.
Impact on the GRIDNET Ecosystem
The security implementation which we are about to unravel extend beyond mere technical elegance – it creates a foundation of trust for the entire GRIDNET mining ecosystem. Operators can now be confident that their mining software remains uncompromised, while the network benefits from the assurance that all participants are playing by the same rules.
Moreover, this system establishes a clear path for legitimate improvements to the mining implementation. When developers create optimized versions of the OpenCL kernel, these improvements can be properly validated, tested, and distributed through official channels, ensuring that performance enhancements benefit the entire community rather than creating unfair advantages. Whenever an attempt to initialize Core with a non-authentic Kernel file is made - Core would refuse to boot.
Technical Implementation
Self-Integrity Verification
The Core executable now performs self-validation using the following process:
- Hash Calculation: The executable computes its own SHA-256 hash from its code section
- Hash Comparison: Compares against an ChaCha20-Base58-check encrypted-encoded expected hash
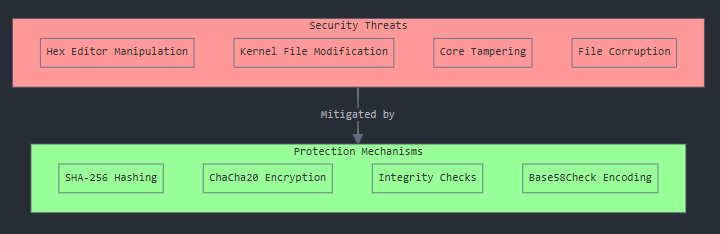
- ChaCha20 Protection: Expected hash is stored with ChaCha20-Base58-check encoding to prevent simple hex editor manipulation
// Simplified example of protected hash verification
const char* encodedHash = "\x2F\x11\x06\x14..."; // ChaCha20-encrypted and Base58-check encoded
std::string actualHash = computeCodeSectionHash();
if (decodeAndCompare(encodedHash, actualHash) != MATCH) {
return INTEGRITY_FAILURE;
}
Core Components and Security Challenges
Understanding OpenCL Kernels and Their Critical Role
At the heart of GRIDNET’s mining process lies a special type of program file – the OpenCL kernel. While the Core executable manages your mining operation’s overall logic, the real computational heavy lifting happens in these *.cl files. Think of them as specialized programs that speak directly to your GPU or CPU, orchestrating the complex calculations required for Proof of Work mining.
The Power of OpenCL
OpenCL (Open Computing Language) serves as a universal language for parallel computing. When you start mining, GRIDNET Core loads these kernel files, compiles them for your specific hardware, and deploys them to perform millions of hash calculations per second. The kernel files contain precisely optimized instructions that determine how your mining hardware:
- Constructs candidate blocks
- Performs complex cryptographic operations
- Searches for valid nonce values
- Validates potential solutions
This is where the challenge begins. Unlike the Core executable, these *.cl files reside as separate components in your system. They’re plain text files containing OpenCL code that gets compiled at runtime. This accessibility, while great for transparency and optimization, presents unique security challenges.
Why Kernel Integrity Matters
Imagine two scenarios:
First, picture a chess tournament where some players have secretly modified their computer opponents to play suboptimally against them. Now imagine a mining network where some operators have tweaked their kernel files for unfair advantages. Both situations undermine the fundamental principle of fair competition.
Second, consider building a complex machine where one crucial component has microscopic defects. Similarly, a slightly corrupted or incorrectly modified kernel file might compile successfully but produce subtle computational errors, potentially wasting hours of mining time without any obvious signs of failure.
These scenarios illustrate why kernel integrity validation isn’t just about security – it’s about protecting operators and ensuring network fairness.
The Technical Challenge
GRIDNET Core 1.5.5 addresses these challenges through a sophisticated kernel validation system. Each official kernel file’s content is carefully hashed, and this hash is securely stored within the Core executable using the same robust encryption and padding mechanisms that protect the Core’s own integrity markers.
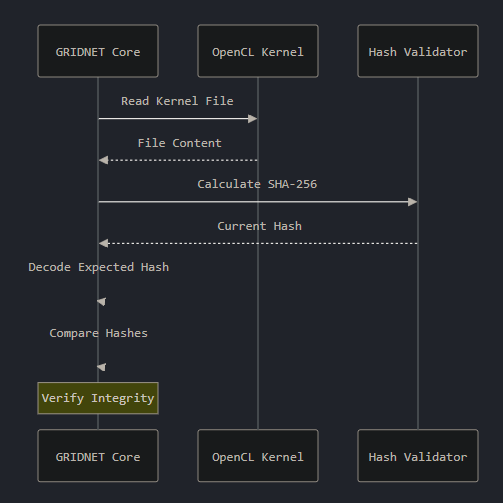
When you start mining, Core performs a comprehensive validation sequence:
- Reads each kernel file
- Calculates its cryptographic hash
- Decrypts the stored expected hash
- Performs a precise comparison
Any mismatch triggers an immediate alert, protecting you from:
- Accidentally corrupted kernel files
- Unauthorized modifications
- Compilation issues that could affect mining efficiency
- Unintended version mismatches
Supporting Innovation While Maintaining Integrity
We understand that many operators are skilled developers who might see opportunities for kernel optimization. We encourage this innovation! However, to maintain network fairness, such improvements should be submitted to the GRIDNET development team for review and inclusion in official releases.
When genuine improvements are discovered, they’re:
- Thoroughly tested across different hardware configurations
- Verified for computational accuracy
- Performance-validated under various conditions
- Released officially with new integrity markers
This process ensures that all operators benefit equally from optimizations while maintaining the network’s computational integrity.
Beyond Simple Validation
The kernel integrity system does more than just validate files – it creates a foundation of trust. When your GRIDNET Core reports successful kernel validation, you can mine with confidence, knowing that:
- Your hardware is running officially vetted code
- Calculations are being performed correctly
- You’re competing fairly with other operators
- Your mining time is being used efficiently
This trust is essential for a healthy mining ecosystem where success comes from computational power and efficiency rather than code manipulation.
Remember, in the world of cryptocurrency mining, integrity isn’t just about preventing malicious behavior – it’s about ensuring every operator can participate in a fair, efficient, and reliable mining network. Through robust kernel validation, GRIDNET Core 1.5.5 helps make this vision a reality.
OpenCL Kernel Validation
Cryptographic Concepts Explained
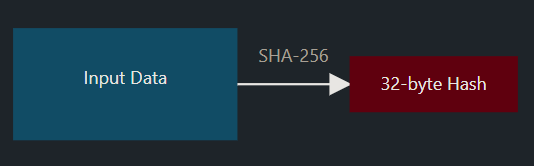
One-Way Hash Transformation
A hash function converts data into a fixed-size string of bytes:
From Theory to Practice: A Live Implementation Journey
The security features we’ve detailed in this article aren’t just theoretical concepts – they represent months of careful implementation, testing, and refinement, all conducted live on our daily programming streams. Since early 2017, our commitment to transparency has resulted in over 190 terabytes of live programming sessions, all preserved by Google for public reference.
During our recent streams, viewers witnessed the complete implementation of this dual-layer integrity system. From the intricate details of PE binary manipulation to the robust kernel validation mechanisms, every line of code was written, tested, and refined with our community watching and participating in real-time.
The result is a comprehensive bootstrap validation sequence that occurs every time GRIDNET Core launches:
- Core executable performs self-validation through code section hashing
- All required kernel files undergo integrity verification
- Detailed status reporting keeps operators informed
- Any integrity mismatches trigger immediate protective measures
This transparent development process not only demonstrates our commitment to security but also provides an unparalleled learning resource for developers interested in cryptocurrency software security. Every decision, challenge, and solution is documented in our stream archives, offering a unique window into the evolution of GRIDNET Core’s security architecture.
We invite you to explore these implementations in our live streams and engage with our development community - here make sure to join our Discord server and check out #Live-Development channel for hourly updates. Together, we’re building not just secure software, but a transparent, collaborative approach to cryptocurrency mining. The concept of mining and thus of cryptocurrency is essential to maintain an appropriate incentive structure in our very fist successful implementation of the concept of a Decentralized Operating System. Within cryptocurrency and without mining - there would be no incentive for Operators to provide their time and other resources. These resources are need to uphold decentralized services, programs and platforms of the future. Platforms which need not be based on selling users’ privacy or by pushing advertisements down their throats.
The integrity validation system in GRIDNET Core 1.5.5 marks a significant milestone in our journey, but it’s just one step in our ongoing commitment to security, fairness, and transparency in the GRIDNET ecosystem.
Looking Forward
This technical Community Update is part of GRIDNET Core Release Notes. The integrity validation system in Core 1.5.5 represents a significant step forward in mining software security, but it’s not the end of the journey. Our team continues to research and develop new security measures, always balancing robust protection with performance and usability.
We’re committed to maintaining GRIDNET’s position as a leader in secure, fair cryptocurrency mining. As threats evolve, so will our security measures, building upon the strong foundation established in Core 1.5.5.
Stay tuned for future updates as we continue to enhance and expand these security features. Together, we’re building a more secure and equitable mining ecosystem for all GRIDNET participants.